
We’ve said it before, and we’ll continue to say it: “Your people are your biggest asset, but they are also your biggest risk.”
Knowing what your trusted insiders are up to is a crucial first step in mitigating the potential risk of an insider threat incident. It is the “detect” portion of our holistic approach to insider threat management (which includes detecting, investigating, and preventing insider threat risks, then addressing them with people, policy, and technology). Limiting access to risk-enabling tools is a valuable next step, working alongside the construction of a comprehensive (but understandable) list of cybersecurity policies. This is where website categorization comes in.
What Is Website Categorization?
The Internet is the first thing that humanity has built that humanity doesn’t understand, the largest experiment in anarchy that we have ever had.
-Eric Schmidt, Google
To say the Internet is a massive place is an understatement. At any given time, the indexed Internet contains around 4.5 billion unique web pages and billions more subpages. Website categorization places what is a countless number of websites into a manageable number of categories to help security teams monitor user activity.
For example, Facebook.com might be placed into the category “social networking” and Bovada.com might be categorized as “gambling.” Website categorization can be immensely helpful for companies. Managing website categories can not only increase employee productivity but also help detect and prevent potential insider threat incidents.
Why Is Website Categorization Valuable?
Website categorization can be useful to security teams in two important ways.
Managing user browsing
Most organizations have an acceptable-use policy that governs employees’ web browsing. Taken directly from a SANS acceptable use template, the verbiage might look something like this:
3.1 Internet Services Allowed Internet access is to be used for business purposes only. Capabilities for the following standard Internet services will be provided to users as needed:
E-mail: Send/receive E-mail messages to/from the Internet (with or without document attachments).
Navigation: WWW services as necessary for business purposes, using a hypertext transfer protocol (HTTP) browser too. Full access to the Internet; limited access from The Internet to dedicated company public servers only.
“Business purposes” is a vague term. As you can imagine, some websites are not what they seem.
Some organizations are strict and may block access to certain websites using a web content filter. Other companies may be more lenient and allow users to use their best judgment. In either practice, security and IT teams often need the ability to detect when a user is going to a website not related to business needs. Categorizing every website that exists is impossible for most security teams. That’s why they need services and products to do it for them.
Detecting and preventing insider threats
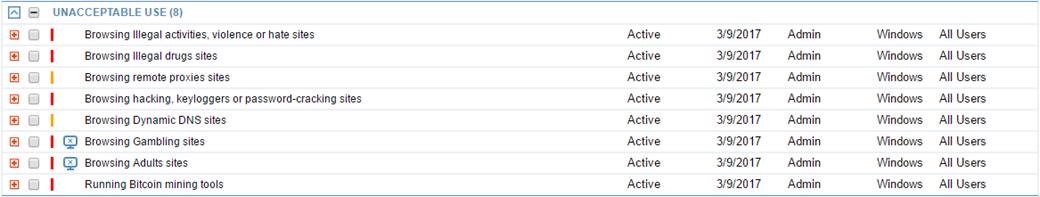
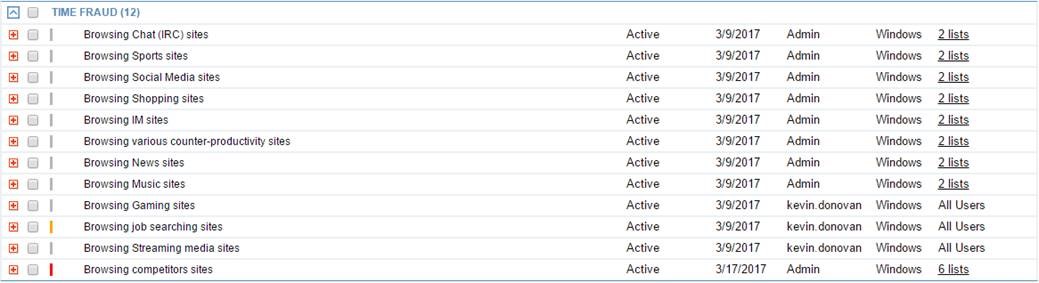
Some companies block sites such as social media or job searching sites as a productivity measure. But you may need to block other categories and websites for security reasons.
Those often include malicious, adult content, and phishing sites—a common criminal practice to obtain sensitive information by tricking employees into inappropriately sharing important information.
How to Categorize Websites Effectively
Tools such as our Insider Threat Management website categorization module can classify more than 28 billion URLs and domains, including those that fall into these types:
- Malicious
- Infected Malicious
- Phishing
- DDNS Services
- Remote Proxies
- Copyright Sensitive
- Legal-Sensitive
- Adults
- Illegal Drugs
- Gambling
- Search Engines & Portals
- Job Searching
- Downloads
- Music
- News
- Sports
- Gaming
- Shopping
- Social Media Sites
- Streaming
- Storage
- Counter-Productivity
- Web Mail
- Chats
- Instant Messaging
- P2P
- Ads
Here are some of the prebuilt alerts in the ITM Threat Library that use website categorization.
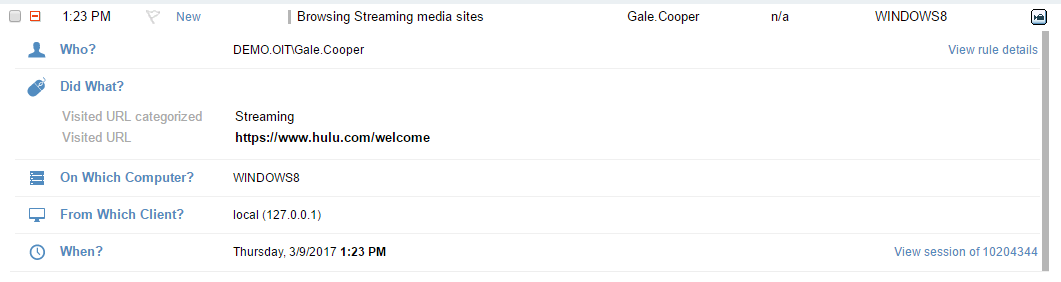
For example, here is what the Proofpoint metadata would look like when a user goes to the video streaming site Hulu.com:
Want to Learn More?
Now is as good a time as any to start learning about website categorization. Proofpoint ITM can help you mitigate risk of an insider threat incident and ensure that your people stay productive.
